Deet Diggers

Today it seems that everybody online—from your favorite social-media platform to cybercriminals—wants to know all about you. BYU experts share how to secure your online life.
By Sara Smith Atwood (BA ’10, MA ’15) in the Spring 2021 Issue
Illustrations by Woody Harrington
”Hey, I can’t talk right now,“ the email began. “Can you do me a favor?”
Sent throughout BYU Marriott’s Information Systems (IS) Department, supposedly from then department chair Bonnie Brinton Anderson (BS ’95, MAcc ’95), the message asked admins and professors to buy a gift card and email a picture of the code.
Sounds suspicious, right?
Luckily, these scammers picked exactly the wrong target: the IS Department is home to BYU’s neurosecurity lab, where Anderson and her colleagues—armed with grants from Google and the National Science Foundation—study the intersection of cybersecurity and user behavior.
Some version of this basic phishing scam—an email, apparently sent by a boss or coworker, asking for a gift card, department card, or personal information—has been reverberating through workplaces across the country. Maybe something similar has crossed your inbox. Maybe you’ve even fallen for it.

When interacting in a digital world, we all know it’s best to be wary. But how good are we at distinguishing between legitimate and nefarious requests, especially those for our personal information? And even when a request is legitimate, are we aware of the consequences of sharing personal information with the apps and companies that optimize our daily lives?
Even if you haven’t fallen prey to a phishing or similar scheme or unwittingly allowed an app to track your every move, you may have had personal or financial information leaked in one of the nearly 12,000 data breaches since 2005. “Most people in the United States have had private information leaked in some way,” says Justin S. Giboney (BS ’10, MISM ’10), a cybersecurity professor in the Ira A. Fulton College of Engineering.
Anderson, now a BYU Marriott associate dean, says that while we should expect tech companies to guard our data and use it sparingly, we’d be naive to blithely hand over information and trust that all is well. As citizens of an increasingly digital world, we have a responsibility to be smart about what we share with apps, companies, and individuals online.
Hey, That’s Personal!
The digital world is swirling with requests for your information. Any time you sign up for an app or shop online, you offer up deets: Your name. Your address. Your birthday. Your mom’s maiden name. All of this information can be used to identify you, to set you apart in the sea of online anonymity.
“That data includes all sorts of things,” says IS professor Ryan M. Schuetzler (BS ’10, MISM ’10). “It’s demographic information; it’s information about your job and your kids, where you currently are and the places you have visited, the people in your contacts list.”
Often, you might not mind sharing some of this data in return for a service. Schuetzler lets Google Maps track his location because he likes to remember where he’s been, and he gives his Strava app access to track how far he runs. Storing credit card info and purchase history on your Target app is convenient, and letting Mint or YNAB track your spending helps you budget.
But once you’ve shared info, even with a legitimate company, it can be hard to know where that data will end up—especially if you didn’t read the terms of service. Will it be sold to other companies to target you with ads or to political groups that want to influence you or to government bodies that want to keep tabs on your behaviors? And what if the data gets hacked?
“Much of our data we so easily and willingly hand over,” Schuetzler says. “It’s easy to lose track of that data because of how many ways we give it away.” Scammers take advantage of that willingness to share, posing as a business you trust to trick you into giving them information like your credit card number, social security number, banking information, or other details, which can be sold piecemeal on the dark web or used to steal money and identities.
We don’t need to be computer geniuses to keep our data safe, says IS professor Jeffrey L. Jenkins (BS ’09, MISM ’09). He says the bad guys are “going to try to hack a system or guess passwords at billions per second or send phishing emails to get the 20 percent who have the weakest security.” He says it’s a matter of not making ourselves “low-hanging fruit” for hackers.
The Privacy Paradox
Ask typical internet users how much they care about keeping their details private, and they’ll tell you they care a lot. But their behavior says otherwise. Researchers call it the privacy paradox.
“We ask people if they would disclose information in a given scenario, and everybody says, ‘I would never do that,’” says IS professor Mark J. Keith (BS ’03, MISM ’04). In his research Keith tested that resolve by creating an app that rewarded users for sharing personal info and was surprised at how willing they were to provide details in return for a perk. “You say, ‘Well, here’s a 25-cent coupon,’ and suddenly it’s, ‘Here’s all my information—take it!’”
And we’re not great at taking the simple steps that might keep us safe: we reuse passwords, share our email address in return for freebies, and ignore browser security warnings and system updates meant to protect us from hackers.

Why are we so inclined to let our guard down? It’s not that we’re lazy or ignorant, says Anderson; it’s the way our brains are programed. She is reminded of teaching her teenage daughter to drive last summer: “New drivers are on edge about everything,” Anderson says. “And they need to be until they can learn what to tune out. Life is too hard to live hyperfocused on everything, so our brains figure out what to tune out and what is critical.”
Anderson’s neurosecurity research has shown that users are prone to ignore security warnings and software updates and to allow apps access to location without realizing it. She’s also used eye-tracking technology to map user eye movements, discovering that simple clues marking a suspicious email—typos, incorrect logos, inconsistencies in links and domain names—are easily missed.
Anderson and her team are working with industry leaders to make software security more intuitive—they’ve already influenced updates to the Google Chrome browser. But again, we aren’t off the hook.

Hacker Heists
The final was an elaborate escape room set up in the empty classrooms and hallways of the former Provo High School. To get out, students had to hack a Furby, navigate string “laser beams,” and break into a wireless computer system. It was the culmination of Information Security Management, in which Jenkins teaches grad students penetration testing—the hacking skills used to evaluate an organization’s weaknesses.
Students in the class are always surprised, Jenkins says, at how easy it is to guess a weak password or break into a computer with poor virus protection. A would-be hacker often needs little more than a 30-minute YouTube tutorial to learn how.
By understanding common attacks, these students are learning how to better thwart data thieves. Basic familiarity with the methods of hackers and scammers can help the rest of us, too. Here are some of the bad guys’ favorite tools:
Phishing
A scammer poses as a real company to trick you into sharing personal details through emails, text messages, or even phone calls (“We’ve been trying to contact you about your car warranty”).
Phishing is becoming more common—and trickier to spot. “Within the past month, I’ve had emails that looked legitimate from Apple, Amazon, Netflix, and Venmo,” says Anderson. Even so, there are telltale signs that reveal a fake. Check for typos in the email body, address, or company name. Be especially wary of any email that offers an unearned benefit (like money for a return you never requested), asks you to correct information in your account, or asks for personal information.
On a computer browser, you can hover the cursor over an emailed hyperlink to see where it’s pointing you; on a smartphone, it isn’t so straightforward. A best practice is never to click on emailed links that purport to take you to your accounts. Instead, navigate to the web pages through your browser.
Spear Phishing
Spear phishers craft a targeted attack. They might use info about you they can easily find online—the ages of your kids or an interest in road races—to customize a phishing email, maybe one selling toddler toys or promoting a 5K.
Like the gift card scheme that hit Anderson’s department, spear phishing uses relationships (such as work reporting lines) to give fake emails more credibility. For instance, Anderson has had research paper coauthors report phishing emails “sent” from her. “Someone scraped information from websites where our publications are and knew which people might be expecting an email from me,” she says.
To ward off social-engineering attacks, it’s best to verify the identity of anyone asking for money, personal info, or sensitive details about an organization.
Web Scraping
Web scrapers are algorithms that crawl through the internet, harvesting data. Some tools can be used for research, while others collect email addresses and personal data for nefarious purposes, like spear phishing or guessing passwords. The CeWL attack, for example, “will crawl all over your social-networking profile and gather all the personal information it can,” says Jenkins. “Then it’s going to combine that personal information in a variety of ways to come up with a custom list of potential passwords.”
You can limit how much personal information is readily available by adjusting social-media privacy settings and accepting only “friends” you personally know. Even then, assume that anything you post is public. Be careful what you share about your kids—especially avoiding posting their full names and birthdates—and steer clear of “about me” quizzes, which are great fodder for cracking your passwords.
Malware
A common kind of malware is “adware,” or software that gums up your computer with ads and pop-ups. Other malware programs scrape your personal data, capture login credentials, track your internet activity, and give intruders access to your files. Ransomware holds your data hostage, threatening to destroy or publicly release it unless you make a payment. Malware often gets in through “free” downloads (“Free software isn’t really free,” says Anderson), links in phishing emails, and out-of-date software and operating systems.
To protect yourself, research any free software before downloading it, keep your operating systems up to date, back up your files, and install reputable antivirus software. “Companies that seem to offer privacy and security protection are some of the worst perpetrators,” Keith says. “If hackers can get you to click on a link, they’ll get you to download software on your machine that will delete your data”—and then ask you to pay hundreds to “fix” your computer.
What Our Apps Know
A few years ago, Keith asked his students to download and open an app he’d created.
“It does nothing, gives you nothing,” he told them. “It’s just a plain white screen.” His app would collect the same data that was available to any other legitimate app, including tracking their whereabouts (if they had location services turned on) and noting which apps they had installed on their phones.
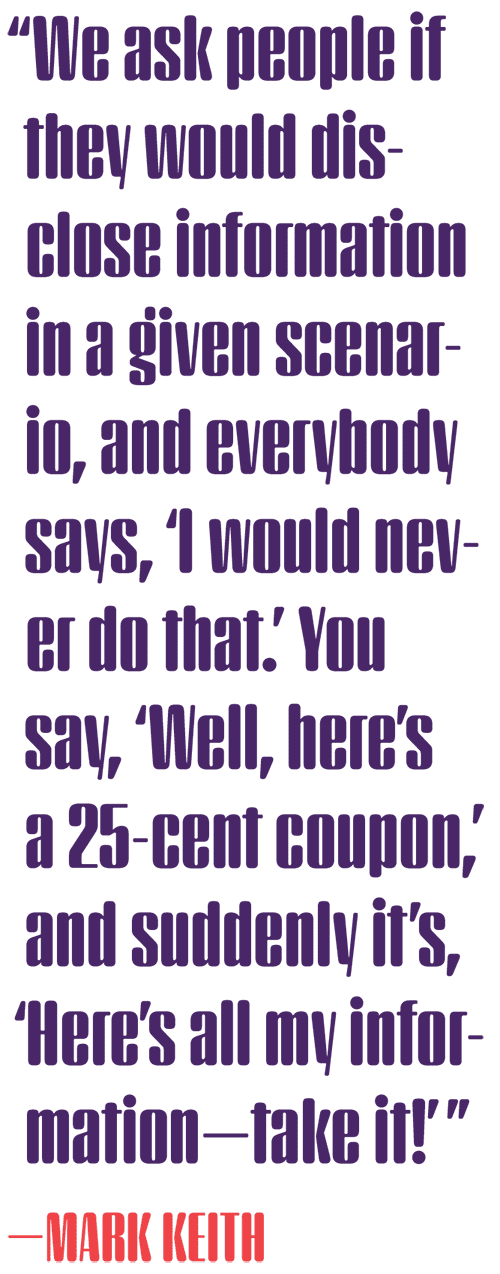
A week later, he told the students to open up his app again. They were shocked to find a list of personal details: the app predicted their gender, employment, relationship status, religion, income, political preference, and ethnicity with surprising accuracy.
“The idea was to show them what was possible,” Keith says. “Immediately, everybody started deleting apps off their phones.”
What’s the risk of sharing data with apps and companies?
For one, it can be annoying—weak industry regulations in the United States make it simple for companies to share or sell customer information, which can lead to targeted emails, web ads, phone calls, and mail you never asked for.
Some of this advertising can be eerily spot on—one day you’re mentioning to your spouse you want to exercise more, and that afternoon gym ads are following you around the internet. Schuetzler, who studies digital assistants, doesn’t think it’s Alexa listening in. Rather, he says, “we are just more predictable than we think we are. We may not even realize the patterns that companies pick up on.” He points to a common saying: “If you’re not paying for the product, then you are the product.” Basically, Facebook and similar apps are free because they use data about what kinds of content you interact with to sell targeted ads. And they aren’t alone.
“You see partnerships form among companies solely to share data so they can get more accurate predictions of what you want to buy next,” Keith says. He personally never gives retail stores his email or phone number, and even threatens to walk when told it’s required.
What about TikTok? Concerns have been raised about the video-sharing app, whose parent company is located in China, where it’s legal for the government to access a company’s data. But Schuetzler doesn’t think “it’s any more of a concern for most people than Facebook or Twitter or Instagram or whatever other social medias you might be using.” Users should be aware that any app that tracks personal data carries some risk and take steps to mitigate it.
Mitigate Your Risk
Not everyone is at equal risk for every threat. High-profile figures have the highest risk of targeted attacks, and people who are newer to the internet—teenagers and older adults—are more likely to overshare on social media or fall prey to phishing schemes.
The average person, says Giboney, is most at risk from data breaches, mainly because they’re so common. Financial risk is offset by credit-card insurance policies, but the loss of personal data and login credentials can put us at risk for identity theft and make other accounts vulnerable. You’re less likely to be hit by spear phishing, he adds, but those attacks can cause more damage.
Given all the risks of interacting online, you might be tempted to pull the plug and jump off the grid completely. But “there are some trade-offs in life for convenience,” recognizes Anderson. She has an acquaintance who goes to great lengths to protect his anonymity—changing phone numbers, avoiding social media, even owning his house through an LLC. Anderson is careful but is not convinced that level of caution is desirable for everyone. The most important thing is to practice basic security hygiene: knowing the red flags of an email scam, using (and not reusing) strong passwords, and being careful about what you share with app developers.
Giboney adds, “with safeguard in place, you will get through just fine and be safe from most attacks.”
Feedback: Send comments on this article to magazine@byu.edu.